The following video in Arabic and subtitled in English.
This blog concerned by subjects of Information Technology and Information Security, which is of interest to both novices and professionals. هذه المدونة تهتم بالموضوعات التي تخص مجال تكنولوجيا و أمن المعلومات و التي تهم كل من المبتدئين و المحترفين.
Thursday, December 31, 2015
Reset forgotten Active Directory 2012 R2 Administrator's Password
What will happen if an Active Directory 2012 R2 Domain
Administrator forgot his password and he did’t create another domain admin
account? don’t worry just follow the steps explained in the following video and
you will successfully reset the administrator password.
The following video in Arabic and subtitled in English.
The following video in Arabic and subtitled in English.
Wednesday, December 30, 2015
Analyzing Email Messages and Determine Sender’s Source IP [Part 2]
In the previous part of Analyzing Email Messages and Determine Sender’s Source IP [Part 1] we had a brief introduction to email systems and we learned together about the email message components, the message envelope, the message header, and the message body.
In this part we will discuss how to analyze the email message and how to determine the sender source IP. Although the message header is the main message component that will used during our work, there is an unfortunate truth “Nearly all message header fields could be forged”. The only trusted header field is the Received: header .
How to view message header?
Viewing message header depends on the email provider and the used email client and usually you will consult the email client manual to know how to view the message header. In the following section we will take some examples of how to view message header?
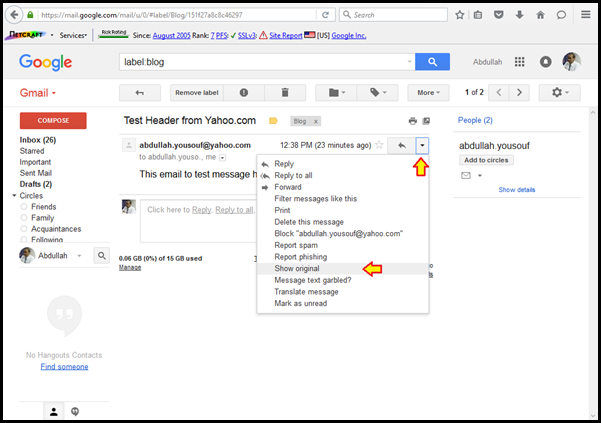
After viewing the email header as the following we will extract important header fields and explain each one of them.
The easiest way for finding the original sender’s source IP is by looking for the X-Originating-IP header field. This header is important since it tells you the IP address of the computer that had sent the email. Most of the times this header is removed by email systems or at least has no value. If you cannot find the X-Originating-IP header, then you will have to go through the Received headers to find the sender's IP address.
In the above header example we added red numbers for all Received: Header fields and as the Received: header read from bottom to top, the numbers started from bottom Received: header field and we can read them in the following order:
(1)Received: from [41.32.28.249] by web310605.mail.ne1.yahoo.com via HTTP; Wed, 21 Oct 2015 07:59:38 PDT
(2)Received: (qmail 83569 invoked by uid 60001); 21 Oct 2015 14:59:38 -0000
(3)Received: from [127.0.0.1] by omp1034.mail.ne1.yahoo.com with NNFMP; 21 Oct 2015 14:59:38 –0000
In this part we will discuss how to analyze the email message and how to determine the sender source IP. Although the message header is the main message component that will used during our work, there is an unfortunate truth “Nearly all message header fields could be forged”. The only trusted header field is the Received: header .
How to view message header?
Viewing message header depends on the email provider and the used email client and usually you will consult the email client manual to know how to view the message header. In the following section we will take some examples of how to view message header?
- Viewing the Message Header in Gmail using Web browser:
Open the message. Click on the "down-arrow" on the top-right of the message and select "Show Original". Below images are snapshots from a message sent from my Yahoo email account to my Gmail account.
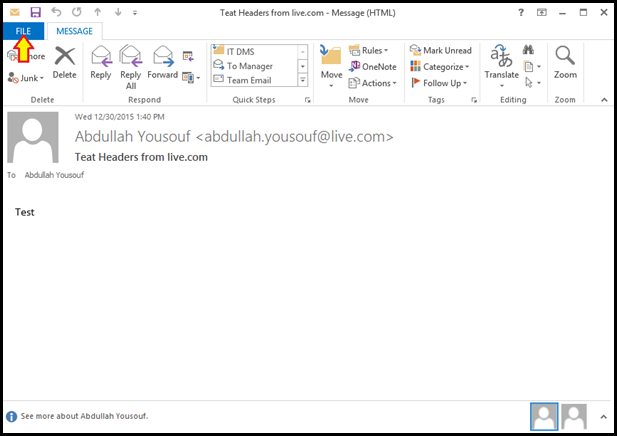
- Viewing the Message Header in Live, Hotmail or Outlook.com email using Web browser:
From the email inbox or messages list. Right-click on the message and select "View Message Source".
- Viewing the Message Header in MS Outlook:
Open the message in MS Outlook. Now go to "View" and select "Message Options" - or "File" -> "Info" -> "Properties".
Look at "Internet Headers".
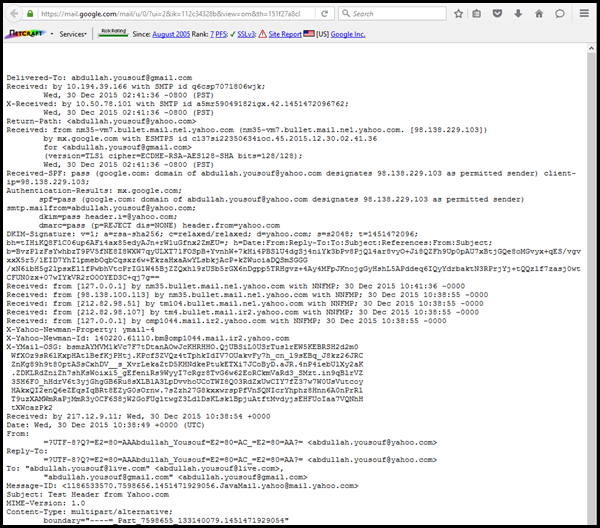
After viewing the email header as the following we will extract important header fields and explain each one of them.
Delivered-To: abdullah.yousouf@gmail.com (7)Received: by 10.194.119.165 with SMTP id kv5csp2398913wjb; Wed, 21 Oct 2015 07:59:40 -0700 (PDT) X-Received: by 10.107.19.106 with SMTP id b103mr8753905ioj.144.1445439580404; Wed, 21 Oct 2015 07:59:40 -0700 (PDT) Return-Path: <atest_2000@yahoo.com> (6)Received: from nm16-vm3.bullet.mail.ne1.yahoo.com (nm16-vm3.bullet.mail.ne1.yahoo.com. [98.138.91.146]) by mx.google.com with ESMTPS id v29si7732890ioi.35.2015.10.21.07.59.39 for <Abdullah.yousouf@gmail.com> (version=TLSv1 cipher=ECDHE-RSA-RC4-SHA bits=128/128); Wed, 21 Oct 2015 07:59:40 -0700 (PDT) Received-SPF: pass (google.com: domain of atest_2000@yahoo.com designates 98.138.91.146 as permitted sender) client-ip=98.138.91.146; Authentication-Results: mx.google.com; spf=pass (google.com: domain of atest_2000@yahoo.com designates 98.138.91.146 as permitted sender) smtp.mailfrom=atest_2000@yahoo.com; dkim=pass header.i=@yahoo.com; dmarc=pass (p=REJECT dis=NONE) header.from=yahoo.com DKIM-Signature: v=1; a=rsa-sha256; c=relaxed/relaxed; d=yahoo.com; s=s2048; t=1445439579; bh=iCCBdD1SchQG2KB dgNVg28FkUjKGk+m8ViOzLA7xlBo=; h=Date:From:Subject:To:From:Subject; b=j4Q/wIDYDfBmAgWocqtZn8O/EM5skUR5v3oiR3 vxwgimyzzz3WgtH2TS/8rl+6U1EPKcSZc4VuArZQSAc9luMBKgW6lLp02ojxy4IIAUmpguZyEVFWZfWpPAOk6fdPfJYG3W5L4EtagY+YlxSa lXWh7CdpmsTTOLf9mK4gYZwZBw8KBdSgL/OpgLlVghpQLAxKpDQmoF3q3YgrEoZc59v7+w0dNq3iB0S+3kxmonj5vVVFbsbVTD25s7dA6zxU ZVZdtJQ7L9E0KmENl5kYLbSYp5uPVWDGnuPbMxnmx3y63x9ufGYhEKnOBY4lUN61EfoqNsZgQQHzUWTG9WMdPWYQ== (5)Received: from [98.138.100.115] by nm16.bullet.mail.ne1.yahoo.com with NNFMP; 21 Oct 2015 14:59:39 -0000 (4)Received: from [98.138.88.234] by tm106.bullet.mail.ne1.yahoo.com with NNFMP; 21 Oct 2015 14:59:38 -0000 (3)Received: from [127.0.0.1] by omp1034.mail.ne1.yahoo.com with NNFMP; 21 Oct 2015 14:59:38 -0000 X-Yahoo-Newman-Property: ymail-3 X-Yahoo-Newman-Id: 446952.69905.bm@omp1034.mail.ne1.yahoo.com (2)Received: (qmail 83569 invoked by uid 60001); 21 Oct 2015 14:59:38 -0000 X-YMail-OSG: _R0c044VM1kcemNNGYZioM44s3FERhgWTGCOCRA94F29fDD xKQIpQQc0DQDMEe6yVQrXA3Jt2AmNQMaVrLno9ENdwYIpS305tRQ6KMDx_ql 8CmwqYpfTvpq7hDN4BfxWT4Kwq7MDEnhUDkOhXM9xC2Yb1NjtDh8ccLAJgJu gNrtyWTDbcqNju1DPGpOCkDrwlyVQDmjx.qb83W8LQjjJ5SN657u_uNRZZ8d 8dqwqkpcaWdELwwSlDlzituowTNpKYHTUhKedlKGEhCoSCBm3uMfMZoLRqRl WUgXvsSEiWpJxH7VI_8ADynXgcE9hHubi7V74FO80gw6H0_pzYaJA0zI1VHu Oh0e0NkdWKd9.htbnSnT4w6Tk2ba84wuN1KlO1pbjwqKEUhQGe_EpzhSZAX7 Rcavy1FiskJJd3IOsJk58JqAbaAVnp_XWoBzPHNlsF0fiv..PW_Se79dBBVX m2VWwlwddtvJFo.x9IDo306_BB2h7B5CI5uJ6dE.Yc.DKwC2auTYP6rtA8WZ 53jsLlArVMvv71dPXzFrn_3L3xL4pq.mAzVgM.lBi9tpt7HhP6InNGali9cN FY1ReCspBB4Ym2El. (1)Received: from [41.32.28.249] by web310605.mail.ne1.yahoo.com via HTTP; Wed, 21 Oct 2015 07:59:38 PDT X-Mailer: YahooMailBasic/802 YahooMailWebService/0.8.203.817 Message-ID: <1445439578.66136.YahooMailBasic@web310605.mail.ne1.yahoo.com> Date: Wed, 21 Oct 2015 07:59:38 -0700 From: atest_2000 <atest_2000@yahoo.com> Subject: Our 0ffers To: Abdullah.yousouf@gmail.com MIME-Version: 1.0 Content-Type: multipart/mixed; boundary="-20674205-2075390769-1445439578=:66136" ---20674205-2075390769-1445439578=:66136 Content-Type: text/plain; charset=us-ascii ---20674205-2075390769-1445439578=:66136 Content-Type: application/pdf; name="doc.pdf" Content-Transfer-Encoding: base64 Content-Disposition: attachment; filename="doc.pdf" |
The easiest way for finding the original sender’s source IP is by looking for the X-Originating-IP header field. This header is important since it tells you the IP address of the computer that had sent the email. Most of the times this header is removed by email systems or at least has no value. If you cannot find the X-Originating-IP header, then you will have to go through the Received headers to find the sender's IP address.
In the above header example we added red numbers for all Received: Header fields and as the Received: header read from bottom to top, the numbers started from bottom Received: header field and we can read them in the following order:
(1)Received: from [41.32.28.249] by web310605.mail.ne1.yahoo.com via HTTP; Wed, 21 Oct 2015 07:59:38 PDT
(2)Received: (qmail 83569 invoked by uid 60001); 21 Oct 2015 14:59:38 -0000
(3)Received: from [127.0.0.1] by omp1034.mail.ne1.yahoo.com with NNFMP; 21 Oct 2015 14:59:38 –0000
(4)Received: from [98.138.88.234] by tm106.bullet.mail.ne1.yahoo.com with NNFMP; 21 Oct 2015 14:59:38 –0000
(5)Received: from [98.138.100.115] by nm16.bullet.mail.ne1.yahoo.com with NNFMP; 21 Oct 2015 14:59:39 -0000 (6)Received: from nm16-vm3.bullet.mail.ne1.yahoo.com (nm16-vm3.bullet.mail.ne1.yahoo.com. [98.138.91.146]) by mx.google.com with ESMTPS id v29si7732890ioi.35.2015.10.21.07.59.39 (7)Received: by 10.194.119.165 with SMTP id kv5csp2398913wjb; Wed, 21 Oct 2015 07:59:40 -0700 (PDT)
From the previous lines order, the first IP address that starts the sending process is 41.32.28.249 which is the source IP address of the email sender. Now we can use any Whois service to find more information about this IP address. Using https://who.is/ for example; we can search for the IP address 41.32.28.249 and the result will give us information about the sender’s ISP (Internet Service Provider) or webhost the IP address belongs as shown in the following image and if it is a spam email, we can send a complaint to the owner of the originating IP address.
Automated Analysis of Email Message Header
Actually there are multiple tools and online services that can automate the process of email message message analysis,
just google it and you will have ton of tools and sites. One of my favorite online email header analysis tools is IP2Location Email Header Tracer,
just copy the entire email header and past it into the Lookup box on the previous link and click on Lookup.
You will receive a nice look analysis just like the following:
There are alot of online and offline tools for email header analysis like:
- https://toolbox.googleapps.com/apps/messageheader/
- http://mxtoolbox.com/EmailHeaders.aspx
- https://www.whatismyip.com/email-header-analyzer/
- http://www.iptrackeronline.com/email-header-analysis.php
- https://testconnectivity.microsoft.com/
Monday, December 28, 2015
Analyzing Email Messages and Determine Sender’s Source IP [Part 1]
Electronic Mail (Email) is one of the critical components of today’s Unified Communication Systems and one of the most used methods to communicate between institutions, companies and individuals. Email used to send and receive messages, documents, media files, meetings … etc.
Sometimes we need to analyze received email messages whether for an incident forensic investigation or as a part of email security protection process. One of the email analysis results is the actual source IP address that originally sent the email message. Before starting to learn together how to analyze email message let’s have a simple and brief introduction about two things:
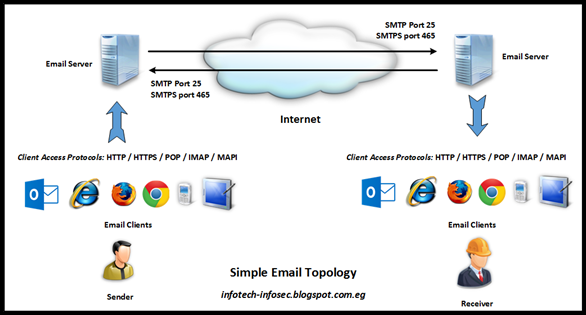
Email systems simply are (client – server) applications where email clients in its basic functionality used by end user to compose new messages and read received messages. Email clients have different types from web clients that uses web browsers to mobile devices and desktop clients like MS Outlook. Email clients accesses email servers using multiple protocols like HTTP / HTTPS / POP(s) / IMAP(s) / MAPI. In the other hand email servers save all sent and received messages into mailboxes and route emails between email servers using SMTP/SMTPs TCP protocols.
Email Message
An email message consists of three components, the message envelope, the message header, and the message body. The email message envelope contains the email address of the "Sender", and the address(es) of the recipient(s).
The message body is the actual message contents and sometimes include signature field. Based on the email client used by end user the message body could be either plain text or HTML format. HTML email messages often include an automatically generated plain text copy as well, for compatibility reasons. HTML message format has the ability to include in-line links and images, set apart previous messages in block quotes, wrap naturally on any display, use emphasis such as underlines and italics, and change font styles.
The message header is structured into fields. Each field has a name and a value. The field name starts in the first character of the line and ends before the separator character ":". You can find information about nearly all email message header fields http://www.iana.org/assignments/message-headers/message-headers.xhtml.
The following list includes the common and mandatory message header fields:
At next part we will discuss how to display email message header and use it for Analyzing Email Messages and Determine Source IP.
Sometimes we need to analyze received email messages whether for an incident forensic investigation or as a part of email security protection process. One of the email analysis results is the actual source IP address that originally sent the email message. Before starting to learn together how to analyze email message let’s have a simple and brief introduction about two things:
- Email System
- Email Message
Email systems simply are (client – server) applications where email clients in its basic functionality used by end user to compose new messages and read received messages. Email clients have different types from web clients that uses web browsers to mobile devices and desktop clients like MS Outlook. Email clients accesses email servers using multiple protocols like HTTP / HTTPS / POP(s) / IMAP(s) / MAPI. In the other hand email servers save all sent and received messages into mailboxes and route emails between email servers using SMTP/SMTPs TCP protocols.
Email Message
An email message consists of three components, the message envelope, the message header, and the message body. The email message envelope contains the email address of the "Sender", and the address(es) of the recipient(s).
The message body is the actual message contents and sometimes include signature field. Based on the email client used by end user the message body could be either plain text or HTML format. HTML email messages often include an automatically generated plain text copy as well, for compatibility reasons. HTML message format has the ability to include in-line links and images, set apart previous messages in block quotes, wrap naturally on any display, use emphasis such as underlines and italics, and change font styles.
The message header is structured into fields. Each field has a name and a value. The field name starts in the first character of the line and ends before the separator character ":". You can find information about nearly all email message header fields http://www.iana.org/assignments/message-headers/message-headers.xhtml.
The following list includes the common and mandatory message header fields:
- From: The email address, and optionally the name of the sender.
- To: The email address(es), and optionally name(s) of the message's recipient(s).
- CC: Carbon copy.
- BCC: Blind carbon copy; addresses added to the SMTP delivery list but not (usually) listed in the message data, remaining invisible to other recipients.
- Subject: A brief summary of the topic of the message (Title). Certain abbreviations are commonly used in the subject, including "RE:" and "FW:".
- Date: The local time and date when the message was sent. Many email clients fill this field automatically when sending. The recipient's client may then display the time in the format and time zone local to him/her.
- Message-ID: An automatically generated field; used to prevent multiple delivery of the message.
- In-Reply-To: This field only applies for reply messages and used to link related messages together.
- Content-Type: Information about how the message is to be displayed, usually a MIME type.
- Reply-To: Address that should be used to reply to the message.
- Sender: Address of the actual sender acting on behalf of the author listed in the From: field.
- Received: when an SMTP server accepts a message it inserts this trace record at the top of the header. The received is the most important part of the email header and is usually the most reliable. They form a list of all the servers/computers through which the message traveled in order to reach you. The received lines are best read from bottom to top. That is, the first "Received:" line is your own system or mail server. The last "Received:" line is where the mail originated. Each mail system has their own style of "Received:" line. A "Received:" line typically identifies the machine that received the mail and the machine from which the mail was received.
- Return-Path: The email address for return mail. This is the same as "Reply-To:".
- Authentication-Results: when a server carries out authentication checks, it can save the results in this field for consumption by downstream agents.
- Received-SPF:Sender Policy Framework (SPF) is a simple email-validation system designed to detect email spoofing by providing a mechanism to allow receiving mail exchangers to check that incoming mail from a domain comes from a host authorized by that domain's administrators.
- Auto-Submitted: is used to mark automatically generated messages.
- Dkim-Signature & Domainkey-Signature: These are related to domain keys. You can learn more about these by visiting: http://en.wikipedia.org/wiki/DomainKeys.
- Mime-Version: Multipurpose Internet Mail Extensions (MIME) is an Internet standard that extends the format of email. Please see http://en.wikipedia.org/wiki/MIME for more details.
- X-Spam-Status: Displays a spam score created by your service or mail client.
- X-Spam-Level: Displays a spam score usually created by your service or mail client.
- X-Originating-IP: This header is important since it tells you the IP address of the computer that had sent the email.
At next part we will discuss how to display email message header and use it for Analyzing Email Messages and Determine Source IP.
Monday, December 21, 2015
Install MS Windows Server 2012 R2 Hyper-V on VMware Workstation v12
Hyper-V
Hyper-V is a Windows Server role that lets you create a virtualized server computing environment where you can create and manage virtual machines. You can run multiple operating systems on one physical computer and isolate the operating systems from each other.
Sometimes we need to build test or proof of concept environments and we don’t have required hardware resources and to take over this obstacle we can build multiple Hyper-V 2012 R2 servers using VMware workstation v.12 or in other words we can build nested virtualized environment by installing Windows Server 2012 R2 Hyper-V on VMware Workstation v.12.
By default VMware Workstation v.12 does not allow installing Hyper-V Role on a virtual machine running Windows Server 2012 R2 and when you try to install Hyper-V Role you will receive the following error message as shown in the following image:
To resolve this issue shutdown the Windows Server 2012 R2 virtual machine we need to follow the next two steps.
Step 1:
Make sure that the “Intel VT-x and AMD-V” Virtualization engine for the virtual processors of the virtual machine of Windows Server 2012 R2 is enabled.
From Virtual Machine settings, click on Processors, under Virtualization engine, check on Virtualize Intel VT-x/EPT or AMD-V/RVI checkbox as shown in the following image and click OK.
Step 2:
From the folder of the Windows Server 2012 R2 virtual machine open the file with ".vmx" extension using a text editor (i.e Notepad) and add the following line at end of the ".vmx" and save the file.
hypervisor.cpuid.v0 = "FALSE"
Start your Windows Server 2012 R2 virtual machine again and try to install the Hyper-V Role. The following video is a full demo for installing MS Windows Server 2012 R2 Hyper-V on VMware Workstation v12https://www.youtube.com/watch?v=8T4VkBjMPGU
Subscribe to:
Posts (Atom)